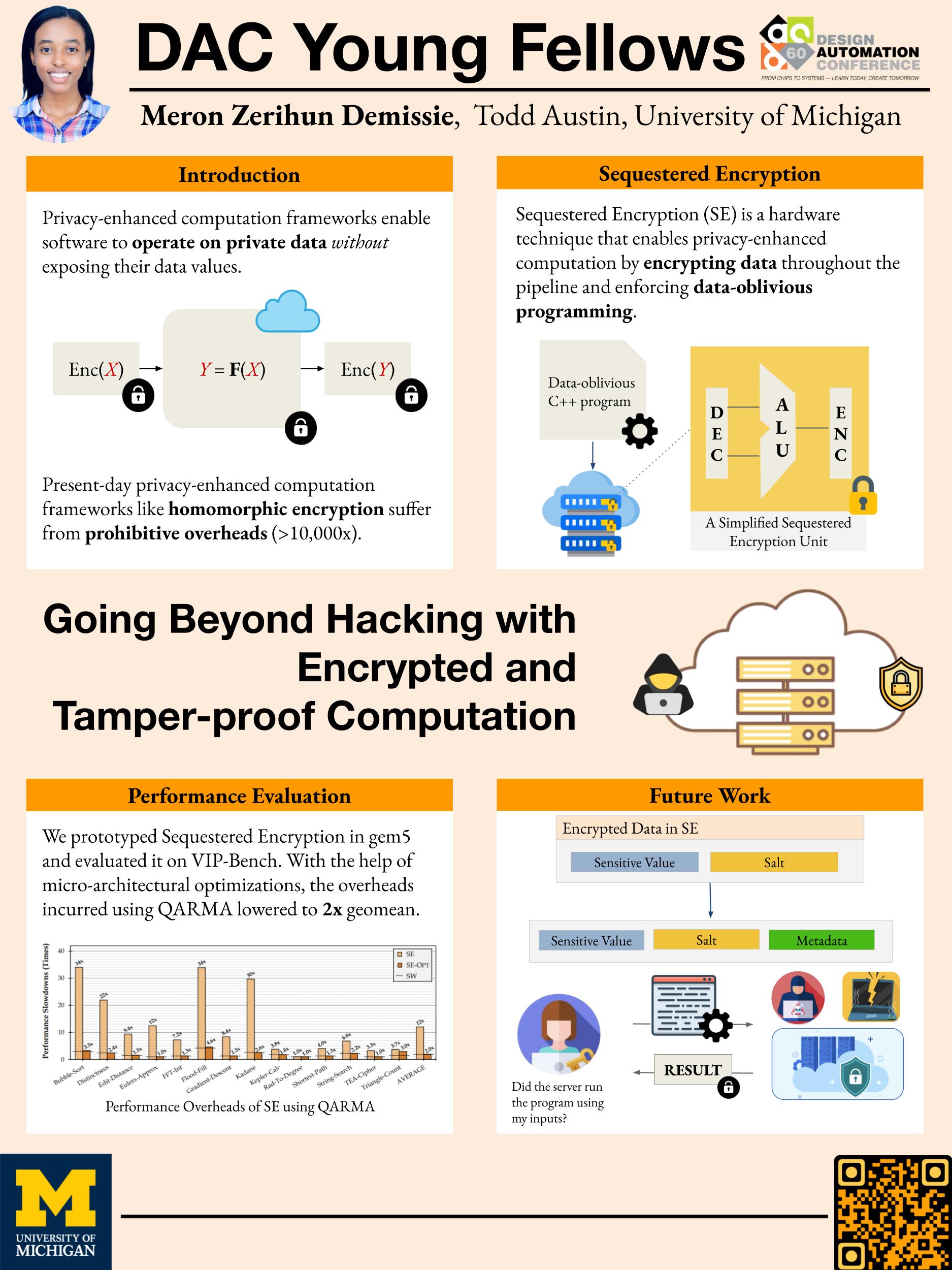
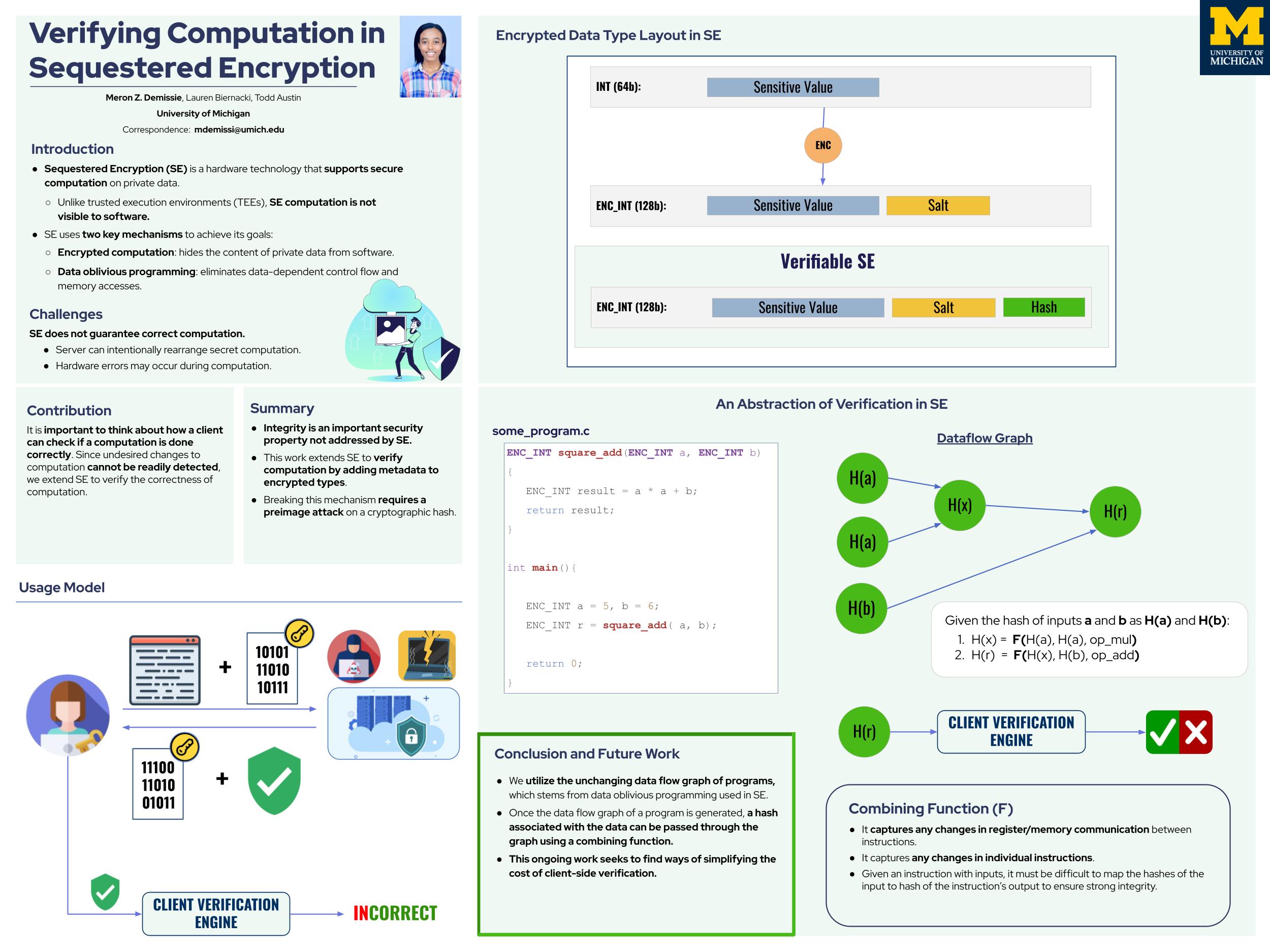
Intro
Hello! My name is Meron Zerihun Demissie. I was born and raised in Addis Ababa, Ethiopia, a country located at the Horn of Africa. Currently, I am pursuing my Ph.D. in Computer Science and Engineering at the University of Michigan. I am advised by Prof. Todd Austin. My research focuses on identifying approaches to prevent vulnerabilities in existing sensitive applications and designing computer systems for private and verifiable computing.
I earned a Bachelor's degree in Software Engineering from Addis Ababa University's Institute of Technology. During my undergraduate studies, I participated in AURA, a research exchange program, where I worked in a team on a project called Privacy Enhanced Computer Architecture, which continues to inspire my current scholarly pursuit.
To learn more about my academic work and other activities, feel free to explore this website and don't hesitate to contact me.